DNS queries have long been transmitted over clear plain text, allowing everyone on the internet to see your online activities. Encrypted DNS has received extensive attention nowadays. However, it has yet been widely supported by softwares, nor operating systems.
Here at OneMole VPN, we strive our best to secure your online activities. Now we're adding a new feature to encrypt all your DNS queries from end to end, without you doing anything.
DNS
What is DNS exactly? According to Wikipedia, it is a name resolving system which basically tells your browser where is www.onemole.com.
When you type www.onemole.com into your browser, it will send a query to your configured DNS server, which will then tell your browser where is the server hosting www.onemole.com, ie. its (IP address). Your browser can subsequently navigate to the IP address and get you to the website.
The DNS can be something automatically configured by your ISP or the public wifi hotspot you're connecting to, or some public DNS you specified.
Problem
So what's the big deal? The problem is all your DNS queries are being sent in clear plain text. It means that anyone connecting to the same wifi hotspot can easily see what website you're visiting. Maybe that gentleman sitting near you in Starbucks is watching all your online activities secretly, just like you're sharing your screen with him.
Besides that, some DNS servers may give you fake IP addresses for the websites you're trying to visit. They may prevent you from accessing certain websites by doing so, or even worse, they may lead you to a phishing website.
You may find instructions from the Internet, telling you to use a reputable DNS server such as 1.1.1.1 or 8.8.8.8. However you can not trust the IP addresses that you obtained even when you have done so. The unencrypted DNS traffic can be easily spoofed by anyone in your network without your notice.
Any solution then? The answer is encryption.
HTTPS
You may have heard of HTTPS already. When you visit www.onemole.com using Google Chrome, you may have noticed the little green padlock on the left of the address bar, telling you that you're visiting an HTTPS website. All your traffic to and from the website has been securely encrypted.
With encryption, the contents that the server sends to your browser can only be decrypted by your browser and then become readable, ensuring only you would see the contents. All other people in your network won't be able to decrypt and read the contents. They will only see some random texts if they try.
Thanks to Let's encrypt and many other contributors, more websites nowadays have deployed HTTPS to protect us.
It seems that we're safe. Are we? No we're not, yet.
DNS over HTTPS
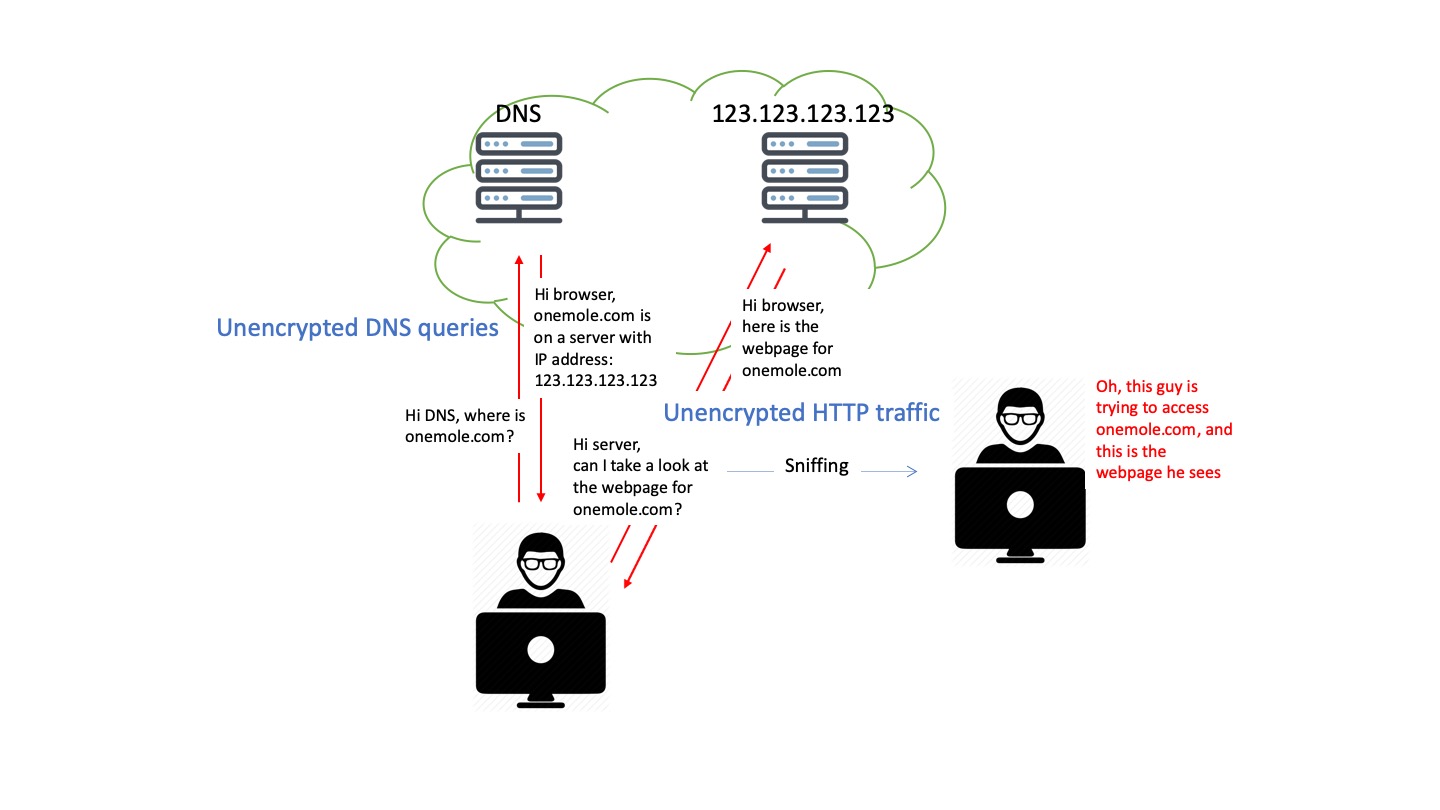
Remember we said that your browser will send an unencrypted query to the DNS server before navigating to the website? Yes, that's the loophole.
HTTPS encrypts the traffic between your browser and the website, but unfortunately not the DNS queries which are being sent before HTTPS encryption takes place. Therefore, although that hacker sitting next to you in Starbucks may not see your OneMole VPN setting details, but he definitely knows you're visiting www.onemole.com, like what is shown in the following illustration.
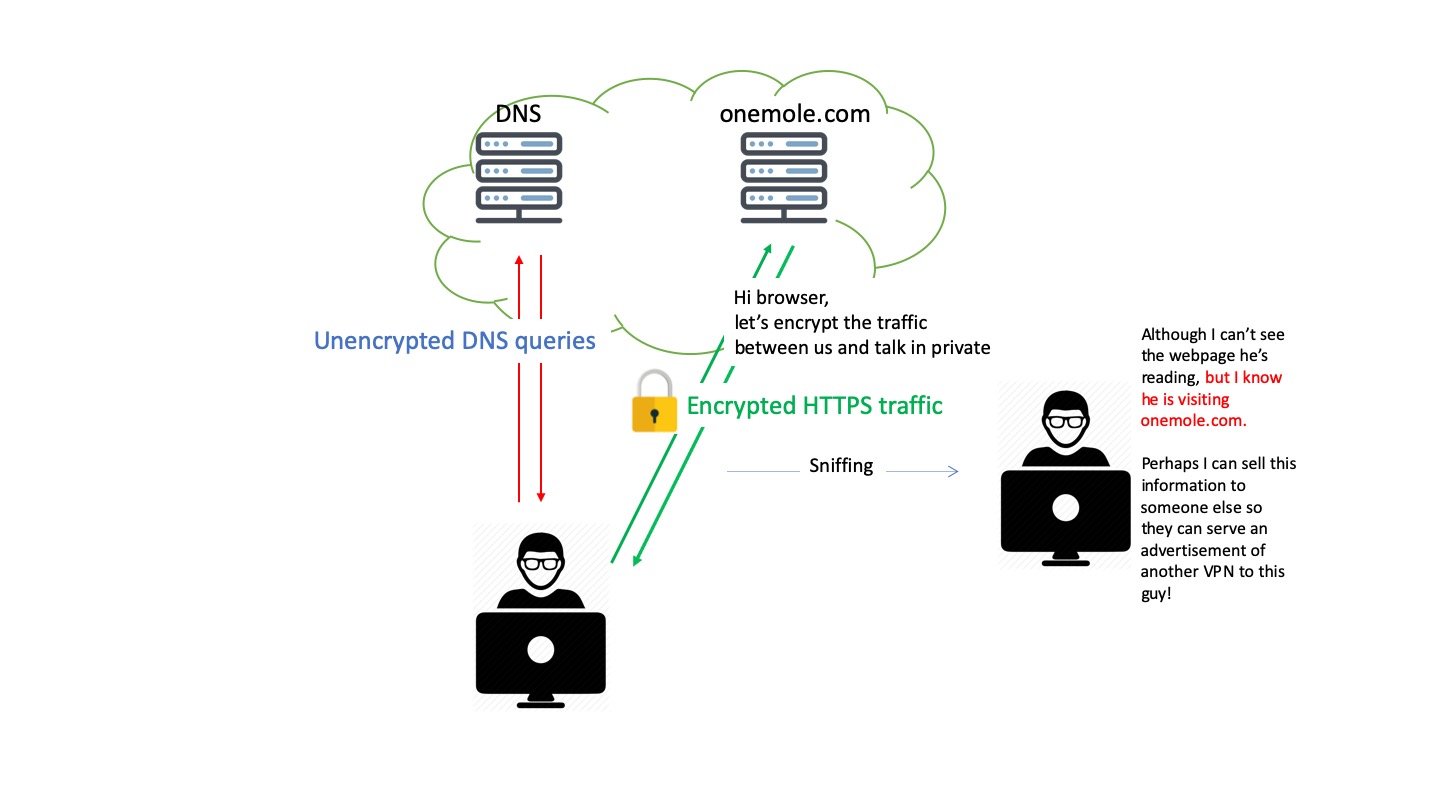
Therefore, people have come up with the idea of using HTTPS to encrypt DNS queries (DNS over HTTPS).
It is indeed an efficient and reliable approach to safeguard the DNS queries. However, this approach has not been well supported by most softwares and operating systems. Unfortunately, we're still vulnerable. But we can protect ourselves with VPNs.
VPN
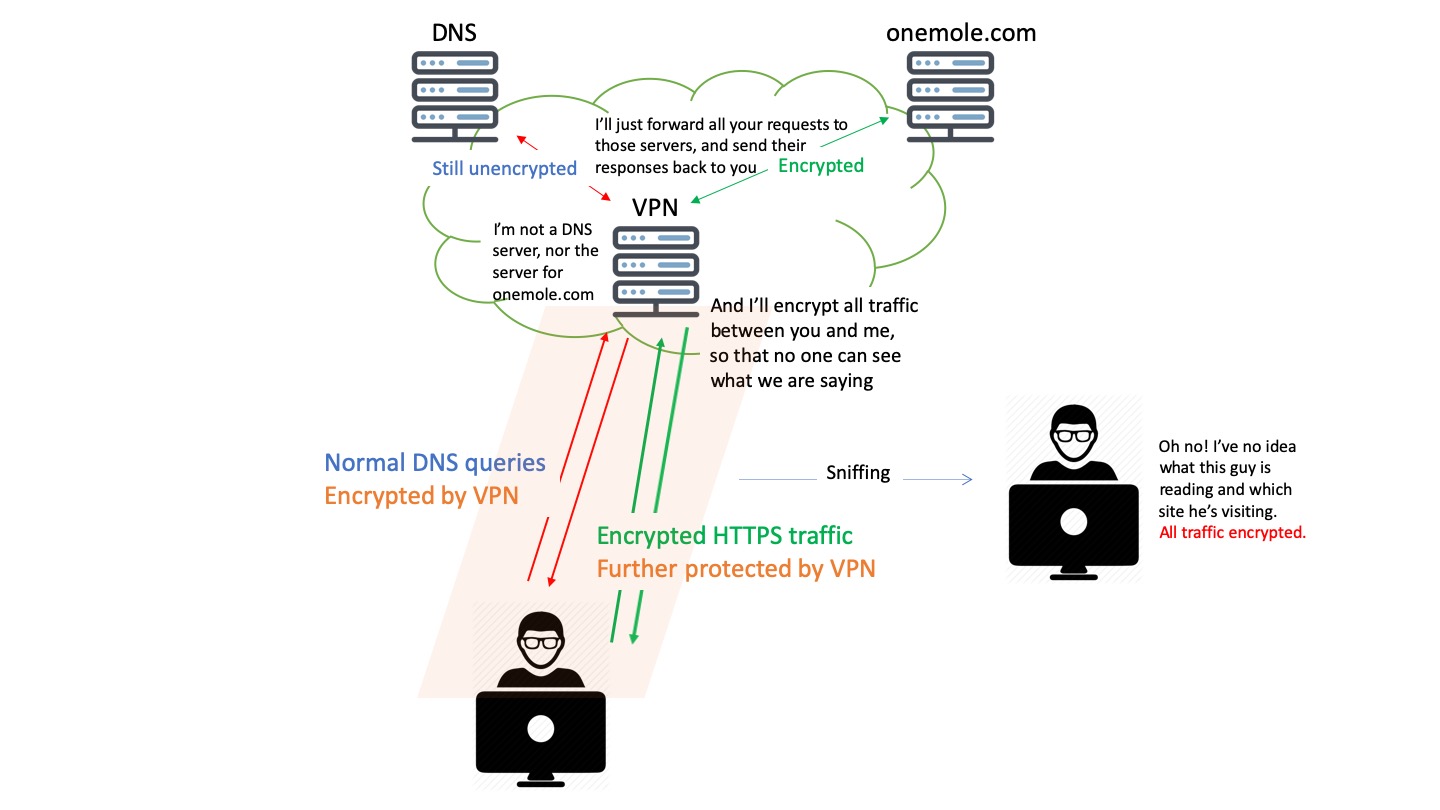
Traditional VPNs will encrypt all your traffic between your computer and the VPN servers. Now the contents from different websites as well as your DNS queries are all inaccessible to that gentleman in Starbucks.
In terms of DNS, now you'll be confident that no one in your network will see your DNS queries, nor anyone can secretly change the IP addresses sent by your DNS server.
OneMole VPN
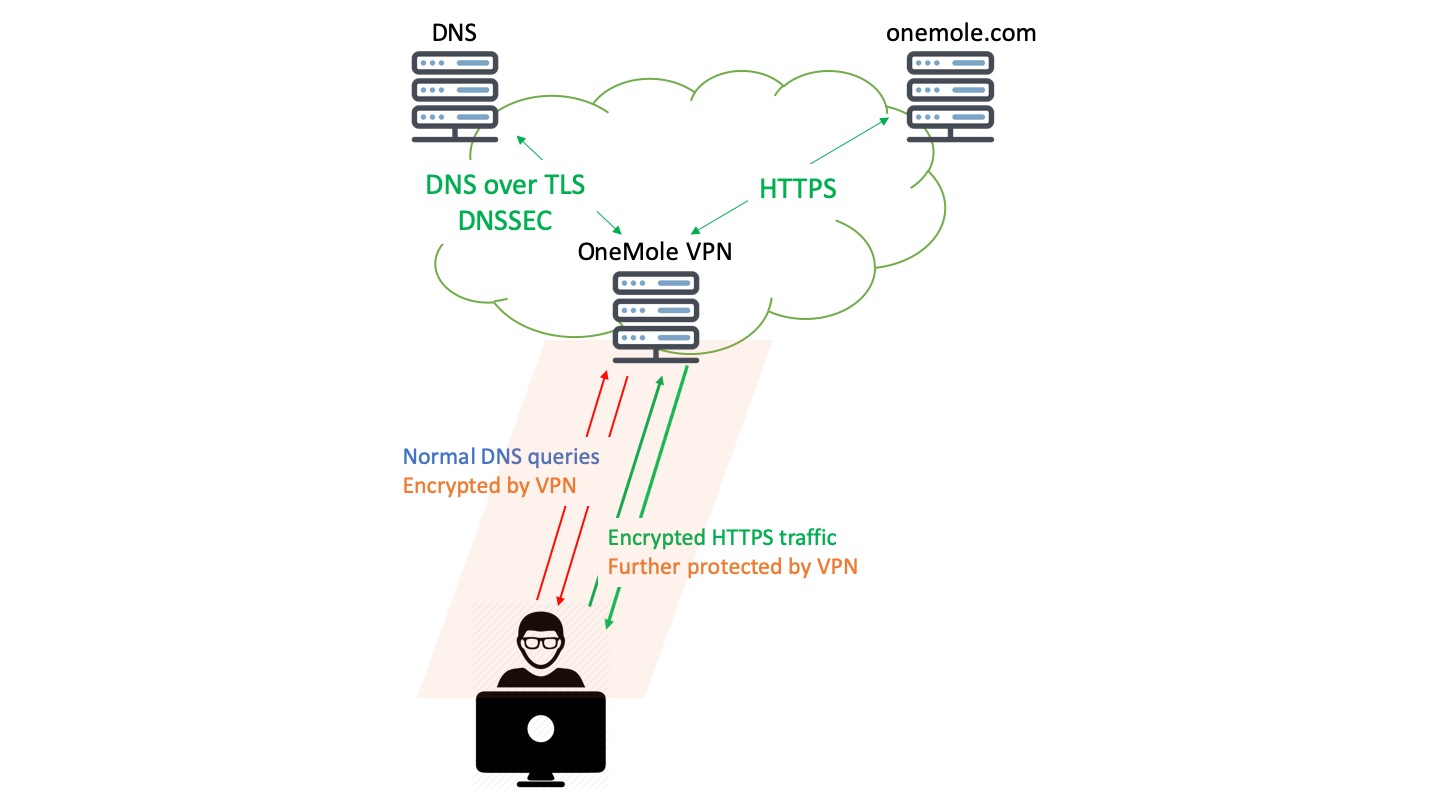
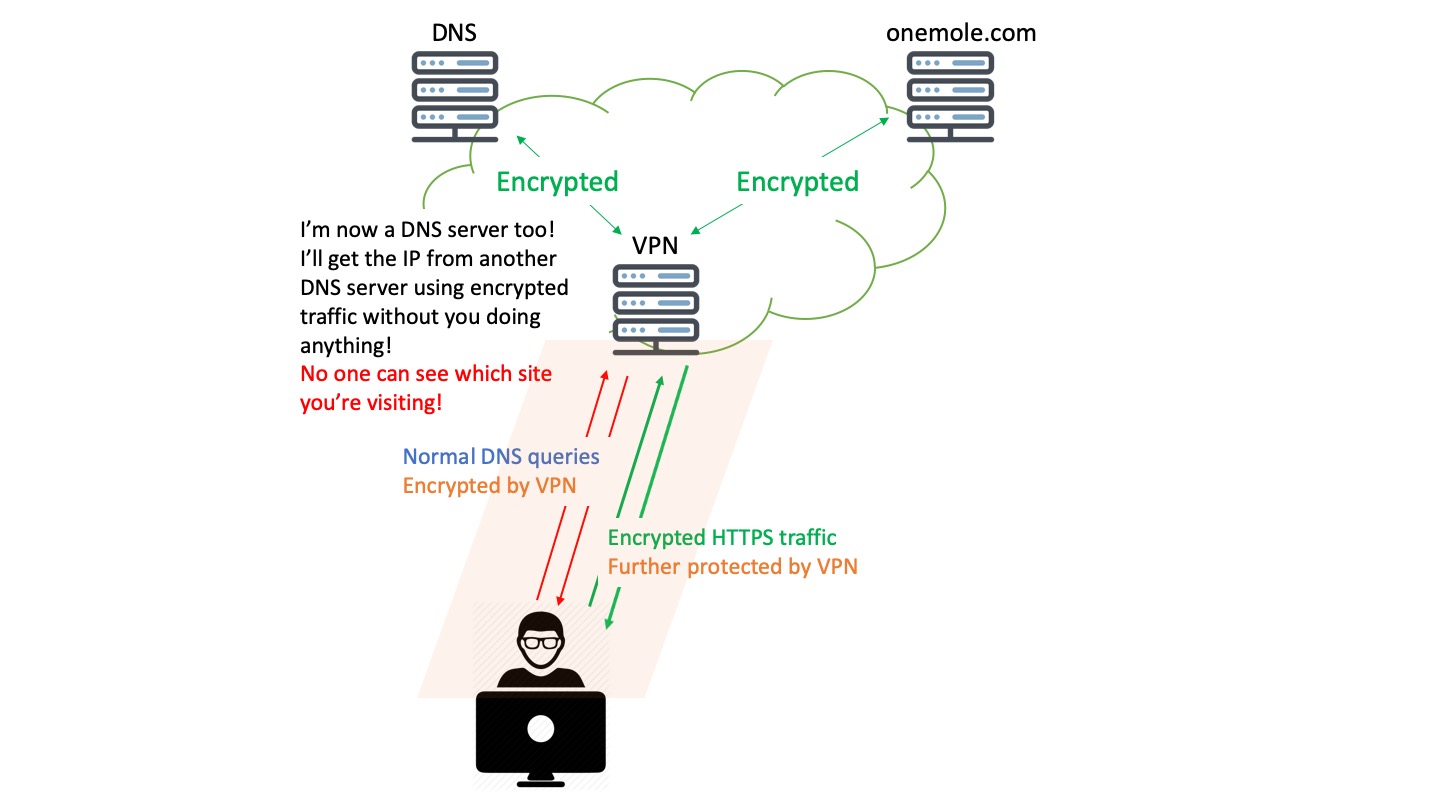
But we don't think that's the end of the story. You may have noticed as well in the last illustration, that once the DNS queries leave the VPN server and are being forwarded to the DNS server by the VPN server, they are still unencrypted. Although not readily accessible, hackers may still be able to take advantages of these unencrypted DNS queries. Therefore, we want to take a step forward to safeguard that too.
With OneMole VPN, we'll host a DNS server on the same server as your VPN, and automatically make your browser use that particular DNS server once you are connected to your VPN.
By doing so, your DNS queries will not leave your VPN server, hence no more unencrypted DNS queries!
On the other hand, we setup the DNS server in such a way that it will ask other reputable and reliable public DNS servers (1.1.1.1 by Cloudflare, and 8.8.8.8 by Google in particular) for the domains that it hasn't seen before, using encrypted traffic (by DNS over TLS). Now the DNS queries and the responses will all be encrypted throughout the whole journey between your browser and the DNS servers.
Even better, our DNS server will verify the answers from those public DNS servers whenever possible (using DNSSEC), just to make sure the IPs that it gets are authentic.
Now we can say that your online activities are well protected.
We care about your online security, so should you.
Sign up today for a private and secure VPN service to protect your personal and business information.